Washington // The hackers that launched a global cyberattack that brought chaos to banks, hospitals and corporations are expected to return and many computers remain at risk.
Experts warned on Saturday that the hackers can still gain easy access to personal computers that lack a security update issued in March by Microsoft to fix the vulnerability in its Windows operating system. The company had labelled the patch as “critical.”
The attack which started on Friday was only stifled when a security researcher disabled a key mechanism used by the worm to spread.
The malware, using a technique stolen from the US National Security Agency, stopped care at hospitals across the UK, affected Russia’s interior ministry and infected company computer systems in countries from Eastern Europe to the US and Asia.
While most organisations did not suffer as much as the UK health care facilities, the incident renewed debate about the risk of governments stockpiling flaws in commercial technology and using them for hacking attacks.
In the UK, 45 organisations in the National Health Service were affected, home secretary Amber Rudd said on Saturday, and hospitals in London, North West England and Central England urged people with non-emergency conditions to stay away as technicians tried to stop the spread of the malicious software.
“There will be lessons to learn from what appears to be the biggest criminal cyber-attack in history,” Ms Rudd said. “Our immediate priority as a government is to disrupt the attack, restore affected services as soon as possible, and establish who was behind it.”
Health care organisations are notoriously slow to apply security fixes, in part because of the disruption caused by taking critical systems offline. That has made them a reliable victim of ransomware attacks, such as that on Friday in which hackers encrypted data on infected computers and demanded US$300 (Dh1,100) in bitcoin to unlock it.
Many security professionals recommend paying the ransom in such cases as the fastest way to get the data back.
Last year an acute-care hospital in Hollywood paid $17,000 in bitcoin to an extortionist who hijacked its computer systems and forced doctors and staff to revert to pen and paper for record-keeping.
Other victims were most likely small and medium-sized businesses. Some larger organisations, such as Spain’s Telefonica SA and FedEx were also infected. A spokesman for Telefonica said the hack affected some employees at its headquarters, but the Spanish phone company is attacked frequently and the effect of Friday’s incident was not major. FedEx said it was “experiencing interference”.
French carmaker Renault halted production at some factories to stop the virus from spreading, while Nissan’s UK car plant in Sunderland, was affected without causing any major effect on business, an official said.
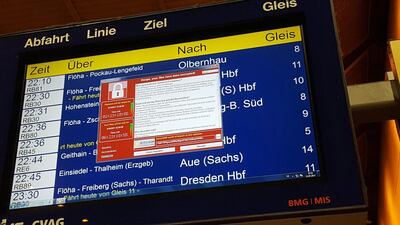
In Germany, rail operator Deutsche Bahn faced “technical disruptions” on electronic displays at train stations, but travel was unaffected, the company said.
Russia’s interior ministry said about “1,000 computers were infected,” which it described as less than 1 per cent of the total.
While any sized company could be vulnerable, many large organisations with robust security departments would have prioritised the update that Microsoft released in March and would not be vulnerable to the attack.
Ransomware is a particularly stubborn problem because victims are often tricked into allowing the malicious software to run on their computers, and the encryption happens too fast for security software to catch it. Some security expects calculate that ransomware may bring in as much as $1 billion a year in revenue for the attackers.
More than 75,000 computers in 99 countries were compromised in Friday’s attack, with a heavy concentration of infections in Russia and Ukraine, according to Dutch security company Avast Software BV.
Microsoft said its March security update had added detection and protection against the new malware after it was reported. “We are working with customers to provide additional assistance,” the company said in a blog posting.
The attack was apparently halted in the afternoon in the UK when a researcher took control of an internet domain that acted as a kill switch for the worm’s propagation, according to Ars Technica.
“I will confess that I was unaware registering the domain would stop the malware until after I registered it, so initially it was accidental,” wrote the researcher, who uses the Twitter name @MalwareTechBlog. “So long as the domain isn’t revoked, this particular strain will no longer cause harm, but patch your systems ASAP as they will try again.”
There is a high-probability that Russian-language cybercriminals were behind the attack, said Aleks Gostev, chief cybersecurity expert for Kaspersky Labs.
“Ransomware is traditionally their topic,” he said. “The geography of attacks that hit post-Soviet Union most also suggests that.”
*Bloomberg